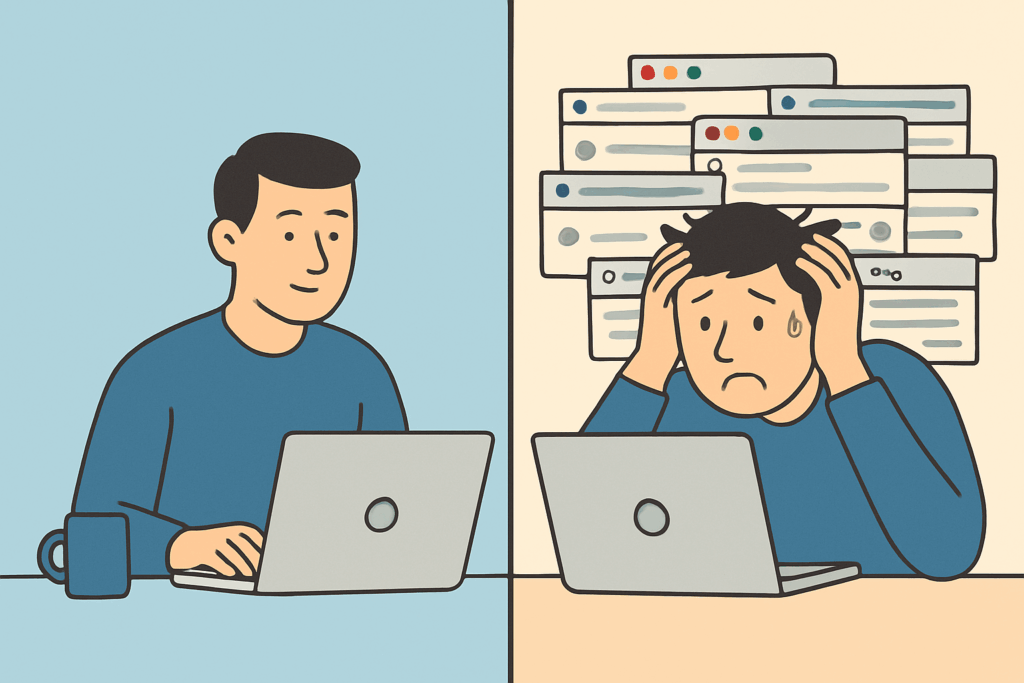
Overwhelmed by endless browser tabs? Learn how to tame the chaos with a clean, practical system that works across Chrome, Firefox, Safari, and any OS—Windows, macOS, or Linux. This guide walks you through smarter tab management, workspace setups, and automation tools to help you reclaim focus and reduce digital clutter for good.
When Meta teased that Llama 4 could support a 10 million token context window, the AI world raised its eyebrows. That’s a serious leap in what large language models can ingest and reason about in one go. But here’s the real question: Is this a revolutionary upgrade?Or is it just a bigger, slower prompt that costs a fortune to run? Let’s break it down—practically, realistically, and from a product builder’s point of view. What Is a 10M Token Context Window? A token is roughly 0.75 words. So 10 million tokens equals about 7.5 million words. That’s equivalent to: 100 full-length…
Perplexity is being hyped as the AI-powered search engine that might replace Google—but does it live up to the hype? Here’s what it does well, where it falls short, and why creators are obsessed with it (for now).
Why does AI sometimes repeat bad answers over and over, getting stuck in a logical loop? It comes down to how AI processes information—not through true reasoning, but through statistical prediction. This article explores why AI’s ‘chain of thought’ reasoning sometimes leads it astray, what its biggest weaknesses are, and what the future holds for making AI actually think smarter.
AI troubleshooting isn’t about just fixing errors—it’s about knowing how to ask the right questions. Here’s how I turned an AI debugging nightmare into a learning experience and discovered better ways to guide AI toward useful solutions.
Design doc culture is killing software development. Instead of writing and testing real code, teams burn months debating hypotheticals in endless Google Docs. This post dives into why prototyping first is the better approach, when a design doc actually makes sense, and how to shift your team toward faster, smarter development.
As silicon processors reach their physical limits, AI is redefining computational scaling. Discover how parallelism, distributed AI, and new economic models are shaping the future of artificial intelligence.
Making videos with AI is easier than you might think. Whether you’re looking for a quick, cloud-based tool or a self-hosted option you can customize, there are plenty of options out there. From simple text-to-video tools like Pictory to advanced setups like Stable Diffusion, this guide breaks down the pros and cons, features, and pricing for each. Whether you’re experimenting or looking to level up your video content, there’s something here for you.
When it comes to 3D printing, the surface you print on plays a crucial role in determining the quality of your prints. Among the various types of print beds, textured print beds have gained popularity for their ability to deliver strong adhesion and aesthetically pleasing finishes. In this blog post, we’ll explore what textured print beds are, why they matter, how to use them, and how to maintain them for the best results. What Are Textured Print Beds? Textured print beds are build surfaces with a rough or uneven texture, typically made from materials like PEI (Polyetherimide), glass, or flexible…
Obsidian is a popular note-taking app that stands out for its focus on local storage, markdown-based editing, and a highly customizable interface. Here’s how it compares to other note-taking apps across various aspects: 1. Data Ownership & Privacy Obsidian: All notes are stored locally, meaning users have complete control over their data. Obsidian doesn’t sync data to the cloud unless users choose to set up their own sync solution or use Obsidian Sync (their optional, encrypted service). Evernote / OneNote: These are cloud-based by default, so while convenient, users are dependent on third-party servers for storing their notes. Notion: Highly…
Effector tilt is a common issue in delta 3D printers that can impact print quality, causing uneven layers and nozzle drag. This guide explains the causes of effector tilt, how to diagnose it through visual inspections and test prints, and offers step-by-step solutions for repair. By understanding these factors and implementing regular maintenance practices, you can ensure your delta printer remains accurate and produces high-quality prints.
A cold pull, also known as an atomic pull, is a crucial 3D printer maintenance technique used to clear blockages and residue from the hotend. This method involves pulling filament out at lower temperatures to effectively remove debris, ensuring consistent print quality without disassembling the nozzle. In this guide, we’ll walk you through when to use a cold pull, the tools needed, and a step-by-step approach to executing it properly for optimal results.
Network segmentation is a critical security strategy for small businesses, helping to isolate network traffic, protect sensitive data, and improve overall network performance. By dividing the network into smaller, controlled segments, businesses can reduce the risk of unauthorized access and contain potential breaches. This post dives into the benefits of network segmentation, offering practical tips on how to implement it effectively using VLANs, firewalls, and monitoring tools. Learn how to assess your network needs, plan segments, and avoid common mistakes to build a secure and efficient network infrastructure.
Securing remote work access is essential for protecting business operations and sensitive data in today’s digital landscape. This post explores how to implement a robust remote work security strategy using VPNs, Multi-Factor Authentication (MFA), and secure gateways. We cover the risks of unsecured remote access and provide a step-by-step guide on configuring VPNs, integrating MFA, and setting up secure gateways. Learn the best practices and tools to create a secure and efficient remote work environment, ensuring your business remains resilient and protected against cyber threats.
Traditional network security models are no longer enough to protect against modern threats, especially for tech enthusiasts managing their own homelabs. Zero Trust architecture offers a solution by focusing on continuous verification, limiting access, and monitoring network activity. In this blog post, we explore the core principles of Zero Trust and provide a detailed, step-by-step guide for implementing it in your homelab. From setting up identity management and network segmentation to using monitoring tools and enforcing least privilege access, we cover everything you need to build a secure, resilient homelab environment.
In today’s digital landscape, a firewall alone is not enough to protect your small business network from evolving threats. As more devices connect and remote work becomes the norm, building a secure perimeter requires a multi-layered approach. This blog post explores why traditional defenses fall short and offers a step-by-step guide to creating a resilient security framework. Learn how to implement zero trust architecture, network segmentation, and advanced monitoring tools to safeguard your business beyond the firewall.
When choosing between cloud-hosted and locally hosted AI, businesses face a crucial decision that impacts performance, privacy, and cost. Cloud-hosted AI offers flexibility, scalability, and access to cutting-edge models, but may come with privacy concerns and recurring costs. On the other hand, locally hosted AI provides greater control over data and lower latency, though it requires a higher initial investment and ongoing maintenance. Understanding the pros and cons of each option is essential for determining the best fit for your needs. Explore the benefits and trade-offs of each approach in our detailed comparison.
Choosing the right AI hardware can be challenging, especially when deciding between Google’s Coral TPU devices and NVIDIA’s powerful RTX 3080ti GPU. Coral TPUs excel in low-power, efficient inferencing ideal for IoT and edge AI applications, while the RTX 3080ti offers unmatched performance for deep learning training and large-scale AI workloads. This post breaks down the features, performance, and best use cases for each option, helping you select the right hardware for your AI projects.
Learn how to set up a local AI development environment using Docker, Jupyter Notebook, and LocalAI models. This beginner-friendly guide walks you through configuring your setup, installing essential libraries, and building a simple AI application for sentiment analysis. Perfect for those new to AI development, it’s your step-by-step path to building and experimenting with AI locally!
Unlock the potential of AI for data analysis in your small business. This guide explores how to use tools like Python libraries (Pandas, Scikit-learn) and pre-built AI services for tasks like customer segmentation, sales forecasting, and sentiment analysis. Learn practical steps to automate processes, uncover insights, and make data-driven decisions for business growth.
Discover the power of open-source AI tools like Hugging Face Transformers, TensorFlow, and PyTorch. This guide explains the benefits of these tools, provides practical examples, and walks you through building your own AI solutions. Whether you’re a beginner or an experienced developer, learn how to create custom models and applications with the flexibility and support of open-source software.
Unlock the power of AI-powered automation with this beginner’s guide! Learn how to set up workflows using tools like n8n or Zapier integrated with AI models like ChatGPT. From automating customer support emails to generating reports, this post walks you through step-by-step instructions and practical use cases to boost productivity and streamline tasks.
Explore the latest advancements in AI models like GPT-4 and Llama 3, and discover what makes them smarter and faster. This post breaks down the improvements in architecture, training techniques, and efficiency, explaining how these advancements enhance real-world applications. Learn how these powerful models are transforming industries and making AI more accessible than ever before.
Regular maintenance is crucial for keeping your 3D printer in top shape. This guide covers essential tasks like cleaning the nozzle, calibrating the bed, tightening belts, and more to prevent common issues and ensure high-quality prints. Establish a maintenance routine to keep your machine running smoothly and extend its lifespan.
Discover the exciting world of exotic 3D printing filaments! This post explores when and how to use flexible, composite, and glow-in-the-dark filaments, offering tips on adjusting settings for optimal results. Learn about the ideal applications for each filament type and how to fine-tune your printer to bring your creative and functional projects to life.
3D printing has become a powerful tool for hobbyists and professionals alike, enabling the creation of functional parts for real-world applications. From custom brackets and gears to enclosures and mechanical components, designing prints that are not only accurate but also strong and durable is essential. This blog post explores CAD techniques and print orientation strategies to help you achieve durable and functional prints that can withstand everyday use. 1. Design for Strength: CAD Techniques for Durability To create functional parts that are robust and capable of handling stress, the design phase is crucial. Proper CAD modeling techniques can significantly influence…
Struggling with stringing and poor detail in your 3D prints? Fine-tuning retraction settings can make all the difference, especially with challenging materials like TPU and PETG. This guide walks you through optimizing retraction distance, speed, and advanced settings to achieve cleaner, more detailed prints. Discover tips for each filament type and learn how to master retraction for better results!
Looking to improve your 3D printing results? Upgrading key components of your 3D printer—like the hotend, extruder, or build plate—can significantly enhance print quality and reliability. This post explores the most impactful upgrades and how they can help you achieve better results with less hassle. Discover the benefits of each upgrade and find out which ones are best for your needs!
Printing with PETG offers a balance of strength, flexibility, and ease of use, but it comes with its own set of challenges. To get the best results, ensure proper temperature settings, optimize bed adhesion, fine-tune retraction to minimize stringing, and adjust cooling for layer consistency. Follow these tips for achieving reliable, high-quality prints with this versatile filament.
Unlock the full potential of Ollama on Windows 10 with this step-by-step guide. Learn how to install the native app, configure network settings, and adjust firewall rules to make Ollama accessible across your local network. Perfect for developers and teams looking to collaborate seamlessly, this guide ensures you can harness the power of AI on multiple devices, enhancing productivity in a connected workspace.